As CI/CD pipelines become critical to software development, securing GitHub Actions workflows is more important than ever. By using CodeQL, developers can identify and mitigate vulnerabilities proactively, ensuring that their workflows remain robust and secure. This guide explores how to leverage CodeQL for securing GitHub Actions, including its features, setup process, and advanced best practices.
GitHub Actions has emerged as a leading CI/CD solution, and with the addition of CodeQL, developers can proactively identify and address vulnerabilities. With the recent deprecation of CodeQL v2 and the launch of v3, it’s essential to update your workflows to leverage enhanced performance, security, and compatibility.
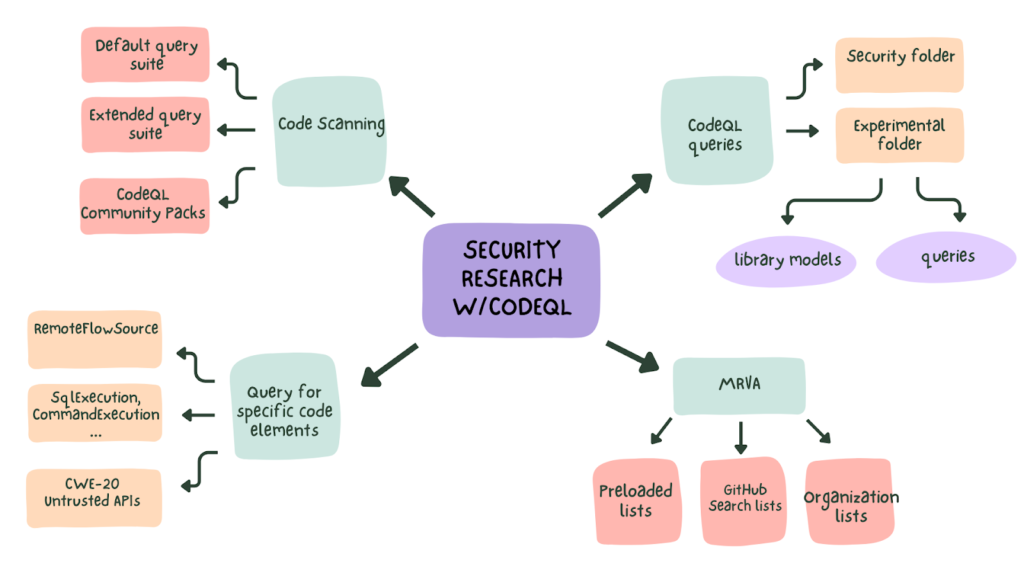
What is CodeQL?
CodeQL is GitHub’s code analysis engine that helps developers identify vulnerabilities by semantically analyzing code relationships. It goes beyond traditional static analysis by allowing custom queries, making it a powerful tool for securing your applications.
Key Features of CodeQL
- Multi-language Support: Analyze JavaScript, Python, Go, and more.
- Pre-built Query Libraries: Leverage pre-defined queries for common vulnerabilities like SQL injection and insecure deserialization.
- Custom Queries: Write your own queries to detect unique issues specific to your codebase.
- Integration: Seamlessly integrate with GitHub Actions and other CI/CD pipelines.
Updating to CodeQL v3
GitHub announced the deprecation of CodeQL Action v2 in January 2025. To continue using CodeQL effectively, you must migrate your workflows to v3. Here’s an updated example workflow configuration:
name: "CodeQL Analysis"
on:
push:
branches:
- main
pull_request:
branches:
- main
jobs:
codeql:
name: Analyze Code with CodeQL
runs-on: ubuntu-latest
permissions:
actions: read
contents: read
security-events: write
steps:
- name: Checkout Repository
uses: actions/checkout@v3
- name: Initialize CodeQL
uses: github/codeql-action/init@v3
with:
languages: javascript
- name: Autobuild
uses: github/codeql-action/autobuild@v3
- name: Perform CodeQL Analysis
uses: github/codeql-action/analyze@v3Best Practices for Securing GitHub Actions Workflows
While using CodeQL significantly improves security, following these best practices can further harden your CI/CD pipelines:
Restrict Permissions: Use the principle of least privilege when configuring workflow permissions. For example:
permissions: actions: read contents: read security-events: writeSecure Secrets: Use GitHub Secrets to securely manage sensitive information like API keys and tokens. Rotate these secrets regularly to mitigate risks.
Evaluate Third-Party Actions: Use only verified actions from GitHub Marketplace or trusted sources. Always specify the exact version of third-party actions to avoid vulnerabilities in updated versions:uses: actions/checkout@v3Limit Network Access: Restrict workflows from making unnecessary outbound connections to minimize the attack surface.
Enforce Code Signing: Verify the integrity of third-party code and scripts used in workflows to ensure they haven’t been tampered with.
Complementing CodeQL with Additional Security Tools
For comprehensive security, integrate other tools alongside CodeQL:
- Dependabot: Automatically scan for outdated dependencies and security vulnerabilities in your project.
- OWASP ZAP: Conduct penetration testing for web applications to identify vulnerabilities in real-time.
- Trivy: Detect container vulnerabilities, misconfigurations, and policy violations.
For example, here’s how you can integrate Dependabot into your workflows:
name: "Dependabot Scan"
on:
schedule:
- cron: "0 0 * * *"
jobs:
dependabot:
runs-on: ubuntu-latest
steps:
- name: Checkout Repository
uses: actions/checkout@v3
- name: Run Dependency Scan
uses: dependabot/dependabot-script@v1Why Upgrade to CodeQL v3?
- Improved Performance: Optimizations for faster analysis and reduced resource consumption.
- Enhanced Compatibility: Support for Node.js 20 and the latest GitHub Enterprise Server versions.
- Security Enhancements: Updated query libraries for detecting emerging threats.
- Future-proofing: Avoid disruptions by aligning with the latest GitHub security standards.
Conclusion: Continuous Security in CI/CD Pipelines
Securing CI/CD pipelines is an ongoing process that requires proactive measures. CodeQL, especially with the updates in v3, is a powerful tool that empowers developers to identify and mitigate vulnerabilities effectively.
By combining CodeQL with robust security practices and complementary tools like Dependabot and Trivy, you can build resilient workflows that protect your applications and infrastructure.
Start updating your GitHub Actions workflows today to leverage the full potential of CodeQL v3 and stay ahead in the battle against security threats.
Resources for Further Reading
- GitHub Actions Documentation
- CodeQL Documentation
- GitHub Changelog: CodeQL v3 Update
- OWASP ZAP Project
- Trivy Documentation
Explore More
- AI Services: Explore our AI services for more details.
- Digital Product Development: Discover our digital product development expertise.
- Design Innovation: Learn about our design innovation approach.




Leave a Reply