Managing Identity and Access Management (IAM) policies across multiple AWS accounts and regions is a critical challenge for organizations operating in a complex cloud environment. IAM Policy Automation is essential for ensuring seamless scalability, security, and governance while minimizing manual errors and inefficiencies.
Listen to the audio version, crafted with Gemini 2.0.
Whether you’re deploying services globally, scaling SaaS products, or enforcing governance, leveraging AWS Systems Manager enables organizations to automate IAM policy management effectively. This approach ensures consistent policy enforcement across accounts and regions while enhancing operational efficiency.
In this article, we’ll explore best practices, the architecture behind IAM Policy Automation, and real-world implementation strategies for managing IAM policies in multi-account, multi-region AWS environments.
The Challenge: Managing IAM Policies at Scale
Why Automate IAM Policy Management?
- Complexity: As organizations scale, managing permissions across hundreds or thousands of accounts becomes increasingly difficult.
- Consistency: Manual changes can introduce discrepancies, leading to potential security risks.
- Compliance: Many industries require detailed auditing of access management.
- Efficiency: Automating repetitive tasks saves valuable engineering time.
Organizations often operate in environments that include:
- Multiple Accounts: Separate AWS accounts for isolation, security, or billing.
- Multiple Regions: Services deployed globally for performance and compliance reasons.
- Dynamic Changes: Frequent updates due to new services, tenants, or compliance requirements.
Solution Overview: AWS Systems Manager Automation
AWS Systems Manager provides a scalable, serverless approach to automate IAM policy management across multiple accounts and regions. Leveraging its automation capabilities, you can:
- Create consistent IAM roles and trust relationships.
- Automate permissions for cross-account resource access.
- Centralize deployment logic, reducing the need for manual intervention.
Key Components
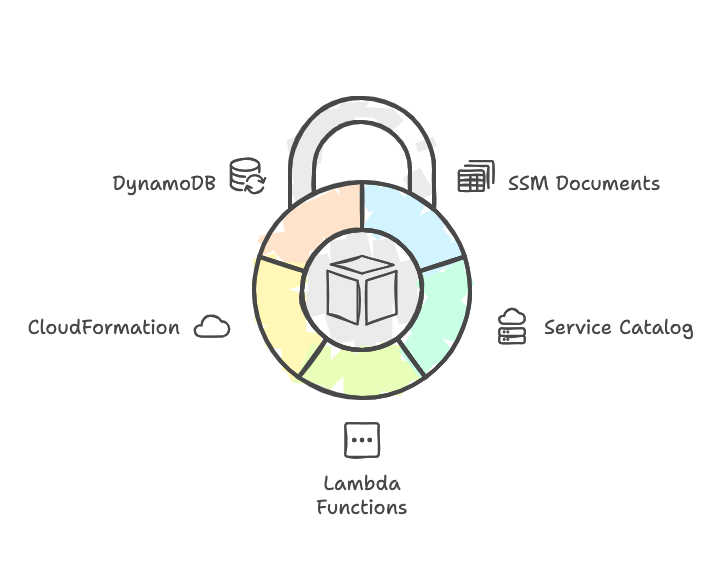
- AWS Systems Manager Documents (SSM Documents): Define automation workflows as reusable templates.
- Service Catalog: Distribute infrastructure-as-code (IaC) templates to teams with version control and governance.
- Lambda Functions: Extend automation workflows for custom requirements, such as dynamic trust relationships.
- CloudFormation: Deploy resources across accounts and regions using consistent, template-based provisioning.
- DynamoDB: Store metadata about deployed resources for reporting and auditing.
High-Level Architecture
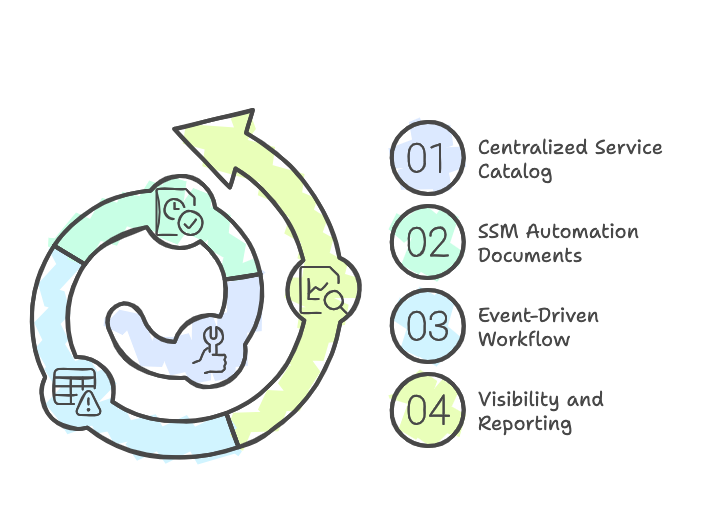
- Centralized Service Catalog:
- Maintain CloudFormation templates for IAM role creation, trust relationships, and resource permissions.
- Provide teams with a self-service catalog to request resources.
- SSM Automation Documents:
- Automate the deployment of IAM policies, roles, and cross-account access configurations.
- Handle dynamic parameters such as ARNs and role names.
- Event-Driven Workflow:
- Use Lambda functions triggered by SSM Automation or Service Catalog events.
- Dynamically configure trust relationships and subscribe resources (e.g., SQS queues to SNS topics).
- Visibility and Reporting:
- Store metadata in DynamoDB to maintain an up-to-date inventory of deployed IAM resources.
- Generate monthly reports for compliance and operational insights.
Key Features of the Automation Solution
1. Multi-Region and Multi-Account Deployment
Deploy IAM roles and trust relationships seamlessly across multiple accounts and regions. Each resource is configured consistently, reducing the likelihood of errors.
2. Dynamic Trust Relationships
Lambda functions dynamically configure trust relationships for cross-account access:
- Automatically subscribe SQS queues to SNS topics across accounts.
- Grant permissions to API Gateway integrations secured with IAM authorizers.
3. Developer-Friendly Experience
- Teams interact with a JSON configuration file defining required resources and relationships.
- A Git-based CI/CD pipeline approves and deploys changes, ensuring compliance.
4. Audit and Governance
- Use DynamoDB as a central repository for metadata on IAM roles, policies, and resources.
- Build dashboards or scheduled reports to monitor resource adoption and usage.
Example Workflow: Connecting an SQS Queue to an SNS Topic
- Triggering Automation:
- A developer creates a Service Catalog request to connect an SQS queue to an SNS topic in another account.
- The request is approved through a Git-based pipeline.
- Resource Deployment:
- CloudFormation provisions the SQS queue in the requesting account.
- A Lambda function triggers an API call to configure the trust relationship and subscribe the SQS queue to the SNS topic.
- Feedback to the Team:
- The SQS queue ARN and other parameters are written to the AWS Systems Manager Parameter Store for use by the requesting team.
- A confirmation email or Slack notification informs the team that the integration is complete.
Real-World Use Case: SaaS Tenant Management
At CyberArk, automation was implemented to manage tenant onboarding and service provisioning across multiple accounts and regions:
- Challenges:
- Provisioning separate AWS accounts for each tenant.
- Establishing cross-account access for shared resources like tenant management and audit services.
- Scaling across 10+ regions and multiple environments (dev, test, prod).
- Solution:
- Automated IAM policy creation and trust relationships using AWS Systems Manager and Service Catalog.
- Reduced deployment time from 18 weeks to under 3 hours.
Best Practices for Automation
- Centralized Governance:
- Use Service Catalog to maintain control over approved infrastructure templates.
- Enforce versioning for all automation workflows.
- Secure-by-Design:
- Limit trust relationships to the minimum necessary permissions.
- Automate auditing of IAM policies to detect overly permissive configurations.
- Scalable Architecture:
- Use event-driven serverless components (e.g., Lambda, DynamoDB) to handle growing workloads.
- Developer Enablement:
- Provide clear documentation and examples to ensure teams can use automation workflows effectively.
- Offer pre-configured blueprints for common use cases like API Gateway access and cross-account messaging.
Future Enhancements
- Expanded Use Cases:
- Automate additional tasks such as certificate creation, DNS configuration, and log filtering.
- Advanced Reporting:
- Integrate with AWS QuickSight or third-party tools to visualize resource usage and compliance metrics.
- Open Source Contributions:
- Enhance community engagement by sharing solutions and inviting contributions on GitHub.
Conclusion
Automating IAM policies and cross-account access in multi-account, multi-region AWS environments is essential for scalability, security, and operational efficiency. AWS Systems Manager, combined with tools like Service Catalog and Lambda, provides a robust foundation for achieving this goal.
By adopting these practices, organizations can reduce deployment times, improve security posture, and empower development teams with self-service capabilities. Whether you’re managing SaaS tenant provisioning or ensuring compliance across global deployments, automation is the key to success.
Ready to Automate? Explore the AWS Systems Manager Documentation to get started.
Explore More
- AI Services: Explore our AI services for more details.
- Digital Product Development: Discover our digital product development expertise.
- Design Innovation: Learn about our design innovation approach.

Leave a Reply